Support for Microsoft Windows XP ended in 2014, 12 years after the software was introduced. The world’s biggest software maker usually drops support for older versions of Windows after a decade or more. Still, an estimated seven percent of the world’s PCs still run on the software. With more than 1 billion PCs believed to be in use, that amounts to an incredible 70 million machines.
Support for Microsoft Windows XP ended in 2014, 12 years after the software was introduced. The world’s biggest software maker usually drops support for older versions of Windows after a decade or more. Still, an estimated seven percent of the world’s PCs still run on the software. With more than 1 billion PCs believed to be in use, that amounts to an incredible 70 million machines.
Given that anachronism, it is remarkable that Microsoft released the patch, or repair, for the largest RansomWare infection in history — just hours after the first attacks were reported.
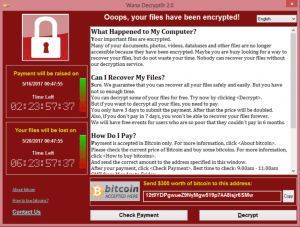
Earlier the same day, the malware called “WannaCry” ripped through hospitals, telecommunications and transportation companies, encrypting files on vulnerable computers without the latest XP patches. The malware demands between $300 and $600 in ransom, payable in the virtual currency bitcoin. To date, limited tracking has determined that around $65,000 may have been extorted from victims.
The spread of the worm does not target a specific geolocation. Nevertheless, a large amount of the infections were found to be in Russia, about 66% of the total attacks. The skew in distribution is likely due to a combination of increased visibility into Russia as well as a likely prevalence of unpatched systems.
However, security analysts studying the infiltration have noticed that a familiar name has surfaced: Lazarus, the nickname for a suspected elite North Korean hacking group.
A code comparison suggests that whoever created WannaCry used some of the same code as the Lazarus Group. Symantec, which is tracking Lazarus, has concurred.
If validated, this means the latest iteration of WannaCry could in fact be the first nation-state powered ransomware. The irony here is that that the vulnerability which WannaCry exploits is believed to have originated inside America’s National Security Agency.
Hackers often reuse code, and malware tools used by Lazarus have been widely analyzed. Pulling code from Lazarus and inserting it into new malware would point the blame toward North Korea, a type of diversion called a false flag.
The clues linking North Korea to Lazarus are rare IP addresses in server logs. Just a month after the devastating attacks against Sony Pictures Entertainment in November 2014, the U.S. government blamed North Korea. The FBI has said an IP address assigned to North Korea was seen in connection with the attack, according to Wired.
Lazarus Group has also been linked to the jaw-dropping financial heists last year involving SWIFT, the financial messaging system used for international wire transfers. In February 2016, Bangladesh’s central bank lost $81 million from its account at the New York Federal Reserve. Only quick intervention, in part based on a spelling mistake by the attackers, prevented Lazarus from walking away with $951 million.
Time for a Digital Geneva Convention
In response to the outbreak, Microsoft is warning against governments stockpiling cyberweapons and has called instead for a Digital Geneva Convention. Will this help?
We strongly concur that the world needs an international digital convention and support with the creation of a neutral international cyber organization and Seattle24x7 firmly supports a pledge from companies to not conduct offensive cyber activities and protect their users from all cyberattacks.
What should you do right now to make sure your organization is protected?
• Install the MS Security Bulletin patches for MS17-010. Please note that Microsoft also released an emergency patch for Windows XP, which is out of support!
• Disable SMBv1.
• Backup your data on a regular basis and be sure to store the backups offline.
• Limit administrative privileges in the network.
• Segment your network.
• Make sure all nodes have security software installed and updated.
• Lastly, stop running Windows XP! It is a 16-year-old operating system which is no longer officially supported by Microsoft.
Kaspersky recommends you upgrade to Windows 8.1 or 10. If you absolutely need to run Windows XP, you can download the emergency patch from Microsoft here: http://www.catalog.update.microsoft.com/Search.aspx?q=KB4012598 [24×7]